Will Citrix Bleed Again? 💉 - MOVEit exploitation spray and pray mode 💦 - Scattered Spider against food and retail 🕷

CitrixBleed2 exploitations possibly already started
Circumstantial indicators suggest that exploitation of the recently disclosed "CitrixBleed 2" vulnerability (CVE-2025-5777) might have already started. Among others, were observed unexplained re-use of valid NetScaler session tokens, authentication events originating from anomalous IP addresses, and immediate post-login reconnaissance. More than 1,200 internet-facing systems remain vulnerable. Similar to the original CitrixBleed vulnerability (CVE-2023-4966), which was exploited at scale in multiple campaigns in 2023, the newly discovered “CitrixBleed 2” enables unauthenticated attackers to exfiltrate session tokens from Citrix NetScaler ADCs and Gateways and take full control of compromised devices.

Another worrisome Citrix vulnerability exploited
Alongside CitrixBleed 2, another critical vulnerability in NetScaler ADC and NetScaler Gateway (CVE-2025-6543) has raised concerns. This memory overflow issue has been observed in the wild and could lead to denial-of-service conditions on Citrix appliances. The vulnerability also affects on-premises and hybrid deployments of Secure Private Access.
[mitigate] Monitor with Qualys QIDs 383418 and 530221 [\mitigate]
Over 2M individuals impacted in a new attack against a food retailer
The cybercrime group INC Ransom has compromised Ahold Delhaize, a leading U.S. network of supermarkets and pharmacies. Impacted entities include Giant Food pharmacies, Hannaford, Food Lion, The Giant Company, and Stop & Shop. The attack resulted in the leak of personal data belonging to over 2.2 million individuals. This incident follows a series of significant attacks on the retail sector, including those attributed to Scattered Spider targeting UK retailers and disruptions at United Natural Foods (UNFI), the main distributor for Amazon’s Whole Foods. INC Ransom is an infamous cybercrime group previously known for compromising Xerox and Yamaha Motors via a Citrix NetScaler vulnerability (CVE-2023-3519).
Swiss government's stolen data offered for free
The ransomware group Sarcoma has breached Radix, a health promotion third-party provider, to exfiltrate 1.3 terabytes of data linked to multiple Swiss federal agencies. The stolen data has been made freely available on a dark web forum. Sarcoma, a rapidly growing Russian ransomware operation, is believed to rely on exploitation of older vulnerabilities for initial access and was also behind the February breach of Unimicron Technology.
Chinese actors uses Ivanti vulnerabilities against France
A Chinese threat group named Houken and associated with UNC5174 has led a large-scale cyber campaign against French organizations across multiple sectors, including government, telecommunications, media, finance, and transportation. Other Western countries have apparently also been impacted. The campaign was first observed in September 2024, though activity may have begun as early as 2023. For initial access, UNC5174 repeatedly leveraged multiple Ivanti CSA zero-days (CVE-2024-8190, CVE-2024-8963, CVE-2024-9380) and, in one incident, a F5 BIG-IP flaw (CVE-2023-46747). Notably, the group has been observed patching by himself these vulnerabilities on compromised systems—likely to prevent rival threat actors from exploiting them. Adopting a hybrid approach, the operation combined the use of open-source tools, commercial VPN services, and a sophisticated custom-developed Linux rootkit. UNC5174, apparently an initial access broker for China’s Ministry of State Security (MSS), has been recently observed in a separate campaign against 70 organizations worldwide which was also based upon the exploitation of Ivanti CSA vulnerabilities.
[mitigate] In Ivanti CSA, ensure dual-homed CSA configurations with eth0 as an internal network; Apply FortiGuard IPS Protections "Ivanti.Cloud.Service.Appliance.datetime.Command.Injection" and “"Ivanti.Cloud.Service.Appliance.reports.php.OS.Command.Injection" [/mitigate]

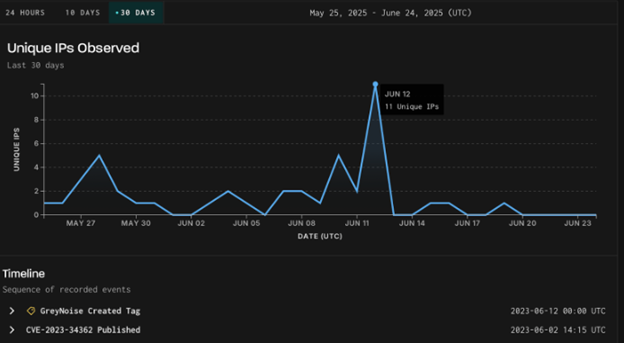
Will MOVEit exploitation resurface?
A surge in scanning activity targeting MOVEit Transfer vulnerabilities has been reported, with 682 distinct IP addresses probing for two known flaws over the past three months. The first vulnerability (CVE-2023-34362) was widely exploited in 2023 by the Clop ransomware group, while no confirmed exploitation has yet been linked to the second vulnerability (CVE-2023-36934). The current campaign began in late May and targets mostly assets based in the US, Europe and Mexico.
[mitigate] Apply Rapid 7 Insight IDR and MDR rules “Suspicious Web Request -Webshell Related To MOVEit Exploit” and “Suspicious Process - MOVEit TransferExploitation” [/mitigate]
Scattered Spider now focuses on Airlines
Following recent attacks on major UK retailers and US insurance firms, the cybercrime group Scattered Spider (UNC3944) has shifted its targeting toward the aviation and transportation industries. Data breaches involving Hawaiian Airlines, WestJet, and Australia’s Qantas have been linked to the group. Scattered Spider is known for its identity-based attacks and sophisticated social engineering tactics, often impersonating IT personnel to escalate privileges and gain access.
NASA mandated to implement risk assessment
The US government has mandated that NASA adopt the NIST cybersecurity risk management framework. A recent report revealed that NASA has not conducted an organization-wide risk assessment, which is considered critical for identifying and mitigating top cyber threats.
- https://reliaquest.com/blog/threat-spotlight-citrix-bleed-2-vulnerability-in-netscaler-adc-gateway-devices/
- https://www.securityweek.com/critical-citrix-netscaler-flaw-exploited-as-zero-day/
- https://www.securityweek.com/ahold-delhaize-data-breach-impacts-2-2-million-people/
- https://www.bleepingcomputer.com/news/security/switzerland-says-government-data-stolen-in-ransomware-attack/
- https://www.cert.ssi.gouv.fr/uploads/CERTFR-2025-CTI-009.pdf
- https://www.greynoise.io/blog/surge-moveit-transfer-scanning-activity
- https://www.bleepingcomputer.com/news/security/qantas-discloses-cyberattack-amid-scattered-spider-aviation-breaches/
- https://www.securityweek.com/nasa-needs-agency-wide-cybersecurity-risk-assessment-gao/
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
