Introducing Proactive Exposure Hunting, the latest enhancement to Zafran’s Threat Exposure Management Platform
SecOps teams face a daunting reality today. A surge in findings of vulnerabilities and misconfigurations that are often fragmented across multiple tools, with a manual process of prioritization and remediation that weighs on resource-constrained teams. We see how these teams struggle to keep up, all while attackers are getting faster and more sophisticated. Meanwhile, these enterprises have invested in an array of security tools, yet still lack a comprehensive picture of where they are most exposed.

SecOps teams face a daunting reality today. A surge in findings of vulnerabilities and misconfigurations that are often fragmented across multiple tools, with a manual process of prioritization and remediation that weighs on resource-constrained teams. We see how these teams struggle to keep up, all while attackers are getting faster and more sophisticated. Meanwhile, these enterprises have invested in an array of security tools, yet still lack a comprehensive picture of where they are most exposed.
Introducing Proactive Exposure Hunting from Zafran
To address these challenges, we are thrilled to introduce Proactive Exposure Hunting, a new solution as part of Zafran’s Threat Exposure Management Platform designed to empower security teams to transition from reactive to proactive defense strategies.
Zafran employs an agentless approach, seamlessly integrating with your existing security tools. Whether it's EDR tools like CrowdStrike, identity controls like Okta, or vulnerability management tools like Tenable or Qualys, Zafran brings them all together. The platform then generates your exposure graph, connecting the dots between your assets, vulnerabilities, identity exposures, control gaps, and the mitigations provided by your existing security controls.
For the first time, security teams can identify the highest-risk exposures and deploy automated responses, transforming the way they manage and mitigate threats.
Automated, High Impact Mitigations
One of the standout features of Proactive Exposure Hunting is the Mitigation module. Here, resource-constrained teams can view a stack-ranked list of actions to mitigate exposure risks. For example, the top recommendation might be a configuration change in your Palo Alto Firewall to counter exploitation of a vulnerability affecting over 7,000 assets.
With a single click, you can create a SOAR incident and trigger a playbook. The mitigation detail is automatically populated, including evidence and specifics of the required actions. The mitigation is then executed using the Zafran playbook, ensuring swift and effective response to identified risks.
.gif)
Assessing Exposure to High-Profile Threats
Security teams often need to assess their exposure to high-profile threats swiftly and accurately. Proactive Exposure Hunting makes this task straightforward. You can view a list of infamous vulnerabilities, such as the RegreSSHion OpenSSH vulnerability, with findings stack-ranked by their risk to your business. This assessment is based on context, including runtime presence, internet reachability, and threat group activity.
Zafran automatically reveals how your existing controls mitigate the risk of exploitation, providing a comprehensive risk context. You can then create workflows to quickly fix the highest risk vulnerabilities with evidence using Jira or ServiceNow VR.

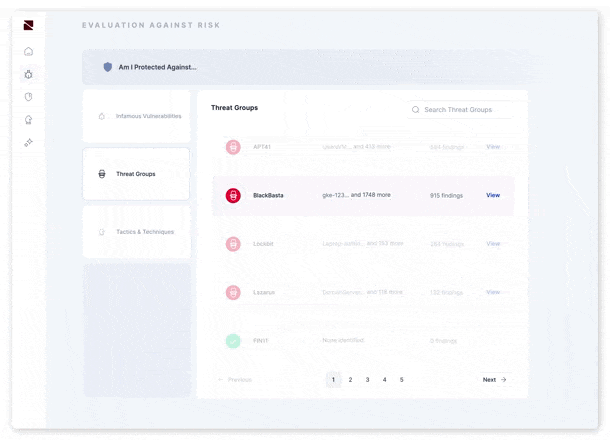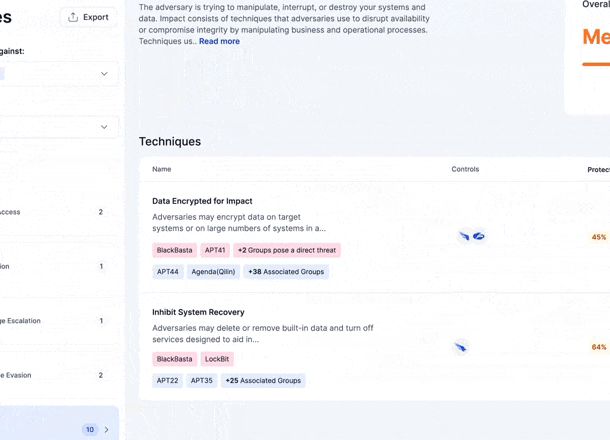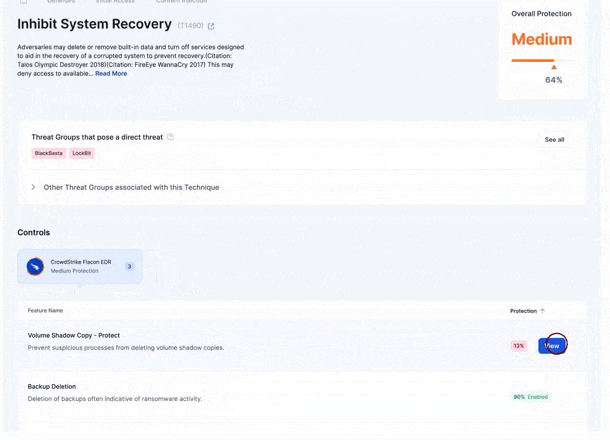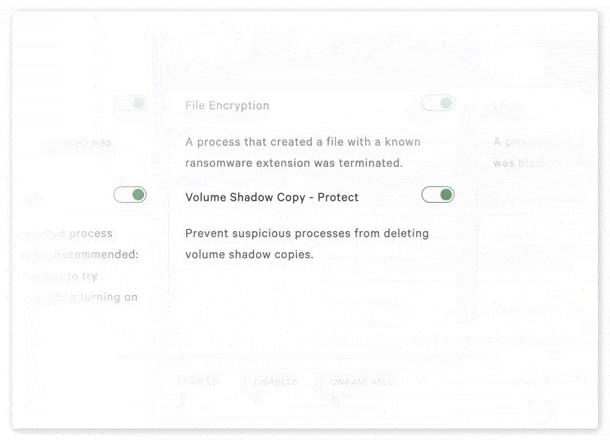
Beyond vulnerabilities, Zafran Proactive Exposure Hunting helps you understand your exposure to high-profile threat actors like BlackBasta, one of the most active ransomware-as-a-service groups.
Within the platform, you can see all known techniques used by these threat actors, mapped to the MITRE ATT&CK framework. For instance, you might discover that CrowdStrike has a feature to protect against a specific attack technique, but it's only 13% enabled. Zafran provides detailed steps to fully enable this feature and, with one click, creates a ticket to implement it in the CrowdStrike console.
Neutralizing identity exposures
Zafran also now helps you understand your exposure to identity attacks by surfacing gaps in identity controls like Okta or Entra ID. With agentless integrations into your identity controls, Zafran can surface exposures such as a root user account without multi-factor authentication (MFA). The platform then presents evidence of the exposure and auto-generates fix recommendations, enabling you to close these gaps quickly and efficiently.
.gif)
Evolving SecOps with Proactive Exposure Hunting
With Proactive Exposure Hunting, Zafran enables your SecOps team to evolve from a reactive response model to proactive exposure hunting. This powerful solution goes beyond our Risk-Based Vulnerability Management capabilities to offer customers a unified platform for threat exposure management, enabling you to take control of your security posture, identify and mitigate risks before they can be exploited, and ensure comprehensive protection against an ever-evolving threat landscape.
Traditional vulnerability management must change. So many are drowning in detections, and still lack insights. The time-to-exploit window sits at 5 days. Implementing a Continuous Threat Exposure Management (CTEM) program is the path forward. Moving from vulnerability management to CTEM doesn't have to be complicated. This guide outlines steps you can take to begin, continue, or refine your CTEM journey.

Request a demo today and secure your organization’s digital infrastructure.
Request a demo today and secure your organization’s digital infrastructure.



