Crowdstrike Crisis follow-up - a new SmartScreen campaign - Vulnerabilities in network edge devices

Crowdstrike crisis
The “Crowdstrike crisis” led to a shutdown of 8.5 million Windows hosts worldwide, impacting various industries and services. The issue, now resolved, was the result of a simple coding mistake in the recent Falcon sensor update, unproperly tested because of a bug in the validator used by Crowdstrike. Various recovery tools have been released, including a Microsoft’s USB drive. Following the incident, dozens of malicious domains referencing to Crowdstrike have launched phishing attacks against impacted organizations, deploying different kinds of malware, infostealers and data wipers.

Crowdstrike's threat intelligence database hacked
A hacker named USDoD has allegedly leaked Crowdstrike’s threat intelligence database, including information and IOCs about threat actors updated to June 2024. Crowdstrike has not denied the breach. USDoD, a hacker operating within the notorious BreachForums, is motivated by both ideological and financial purposes. In the past, it has published data about Airbus vendors, Pentagon’s contractors and others.
Another campaign is using the SmartScreen vulnerability
One of the recent SmartScreen vulnerabilities (CVE-2024-21412) is now exploited by a new campaign deploying infostealers against entities in the US, Spain and Thailand. The flaw allows bypassing Microsoft Defender’s SmartScreen mechanism due to an error in handling maliciously crafted files. It has been previously leveraged by multiple threat actors, including the Russian Water Hydra.
[mitigate]Apply Fortigate IPS rule MS.Windows.SmartScreen.CVE-2024-21412.Security.Feature.Bypass.[/mitigate]
A new cyberespionage group targets vulnerabilities
A new cyberespionage group, nicknamed TAG-100, has compromised organizations in 10 countries and two large Asian inter-governmental institutions. It gained access through the exploitation of vulnerabilities in various internet-facing applications such as NetScaler, F5 BIG-IP, Zimbra, Microsoft Exchange, SonicWall, Cisco ASA, Palo Alto and Fortinet. Last April, the group weaponized an exploit for a vulnerability in Palo Alto Pan-OS (CVE-2024-3400), targeting the education, finance, legal, local government, and utilities sectors in the US. It has also been observed using a vulnerability in the Zimbra Collaboration Suite (CVE-2019-9621).

Twilio authentication app's unauthenticated endpoint
Twilio patched an actively exploited vulnerability (CVE-2024-39891 in its authentication app Authy. The flaw, due to un unauthenticated API endpoint, allows attackers to disclose Authy users’ phone numbers. The vulnerability disclosure comes a recent attack by the infamous ShinyHunters, which published details about 33 million Authy accounts.

Medusa Vs an Israeli newspaper
Medusa ransomware has attacked the Israeli newspaper Globes and is demanding one million USD ransom. In the meantime, the journalists were required to work from home with their personal computer. Medusa, once exploiting RDP vulnerabilities, recently took part in CitrixBleed campaigns.
Adobe Ecommerce flaw exploited in the wild
A new vulnerability in Adobe Ecommerce (CVE-2024-34102) is exploited in the wild. The flaw can be used by an attacker sending a crafted XML document, then achieving arbitrary code execution. Last June, Adobe released an isolated patch tailored for the vulnerability.
[mitigate]Apply NetScaler WAF signature 998464.[/mitigate]
Lviv's heating outage due to a vulnerability exploitation
January 2024’s outage in heating services in the Ukrainian city of Lviv was the result of cyberattack utilizing a new ICS malware. The Russian attackers gained accessed to the networks of the heating services company nine months earlier by exploiting a vulnerability in MikroTek routers.

Telegram's EvilVideo vulnerability
A zero-day in Telegram for Android has been used by an apparently Russian threat actor named Ancryno to send malicious Android APK payloads disguised as video files. The flaw has been used for five weeks before being patched. It requires multiple clicks and user’s acceptance to install unverified apps.
CISA warns about vulnerabilities in edge devices
CISA and the FBI warned against the exploitation of OS command injection vulnerabilities on network edge devices, following the recent attacks leveraging flaws in Ivanti (CVE-2024-21887), Palo Alto PAN-OS (CVE-2024-3400) and Cisco Nexus NX-OS (CVE-2024-20399). Manufacturers are required to “properly validate and sanitize user input when constructing commands to execute on the underlying OS”.
APT41 exploits old vulnerabilities
A new report reviewing a decade of APT41 activities shows that the Chinese group performs both state-directed cyberespionage missions and operations motivated by personal financial gain. The second category explains APT41’s unusual focus on industries such as gaming, entertainment and cryptocurrencies. The group uses various initial access methods, and among those it has commonly exploited old pre-2018 vulnerabilities. Recently, it has also been observed leveraging a Confluence flaw (CVE-2019-3396), which it weaponized 23 days after disclosure.

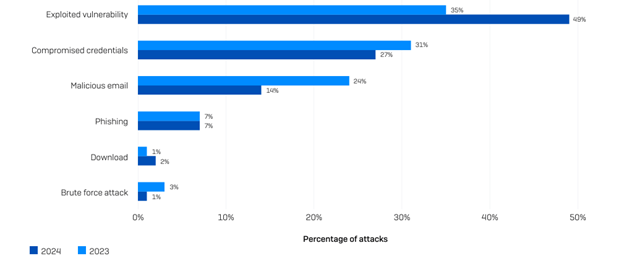
Vulnerabilities used in ransomwares against critical infrastructures
A report about ransomware attacks against critical infrastructures reveals that vulnerability exploitation counts is now behind 49% of the attacks (versus 35% in 2023). The method is particularly common in attacks against the energy, oil & gas and utilities sector.
- https://www.securityweek.com/microsoft-says-8-5-million-windows-devices-impacted-by-crowdstrike-incident-publishes-recovery-tool/, https://techcommunity.microsoft.com/t5/intune-customer-success/new-recovery-tool-to-help-with-crowdstrike-issue-impacting/ba-p/4196959, https://www.securityweek.com/crowdstrike-incident-leveraged-for-malware-delivery-phishing-scams/
- https://www.crowdstrike.com/blog/hacktivist-usdod-claims-to-have-leaked-threat-actor-list/, https://twitter.com/DarkWebInformer/status/1816191236530913290
- https://www.fortinet.com/blog/threat-research/exploiting-cve-2024-21412-stealer-campaign-unleashed
- https://go.recordedfuture.com/hubfs/reports/cta-2024-0716.pdf
- https://www.securityweek.com/organizations-warned-of-exploited-twilio-authy-vulnerability/
- https://www.mako.co.il/news-money/tech12/Article-39aac3f05dfd091027.htm
- https://www.securityweek.com/recent-adobe-commerce-vulnerability-exploited-in-wild/
- https://hub.dragos.com/report/frostygoop-ics-malware-impacting-operational-technology
- https://www.welivesecurity.com/en/eset-research/cursed-tapes-exploiting-evilvideo-vulnerability-telegram-android/
- https://www.cisa.gov/resources-tools/resources/secure-design-alert-eliminating-os-command-injection-vulnerabilities
- https://www.mandiant.com/sites/default/files/2022-02/rt-apt41-dual-operation.pdf
- https://assets.sophos.com/X24WTUEQ/at/75tnw38cqsnrrv56wpwc78k/sophos-state-of-ransomware-critical-infrastructure-2024.pdf
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
